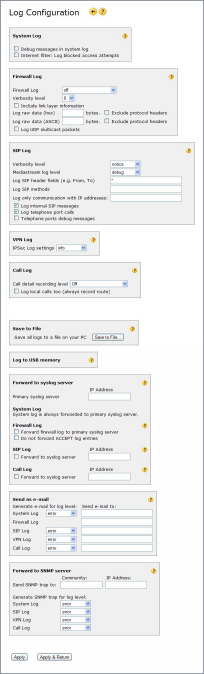
Log Configuration
The log configuration page controls what type of information to record in the unit's different logs and where to send/store those logs.
Severity levels are:
- Emergency
- Alert
- Critical
- Error
- Warning
- Notice
- Info
- Debug
System Log
The system log records generic events that have occurred to the unit.
Usually debug level messages are not logged, to keep the system log clean and readable. When support requests you enable Debug messages in system log to record debug level messages too.
If you have the Internet filter enabled you can log web access attempts blocked by it by enabling Log blocked access attempts.
The system log can be viewed on the system log page or forwarded to various receivers, see below.
Firewall Log
The firewall log records information about packets received and sent by the unit.
The firewall log does not use severity levels, it qualifies packets as:
- Error - internal error when processing packet
- Drop - packet dropped by interface
- Deny - packet denied by firewall
- Accept - packet accepted by firewall rule
Usually the firewall log is turned off - no packets are logged.
| |
|---|
At peak load, some packets may be left out from the log.
If you enable firewall logging, you should consider selecting Show rejected packets as that setting will log all packets stopped by the firewall, but not every single packet passing through.
![]() Try to limit logging by selecting as low log level and verbosity level as possible.
Try to limit logging by selecting as low log level and verbosity level as possible.
You can use the firewall log to see packet data (headers) too. A valuable tool for solving communication problems. You can log up to 64 bytes of packet contents (Log raw data) in hex or ASCII, and exclude common protocol (IP/TCP/UDP) headers so that the 64 logged bytes really are the data you are interested in.
Packets not logged
Multicast UDP packets are not logged, to avoid clogging down the firewall log. One single IPTV multicast channel can contain 500 packets per second! You can enable logging them using Log UDP multicast packets, though.
The communication with Internet Gate's own built-in web server is not logged. It can only be enabled using manually written Additional rules.
The firewall log can be viewed on the firewall log page or forwarded to various receivers, see below.
SIP Log
The SIP log records SIP and telephony related events.
Usually the SIP log does not record events with severity “info” and “debug”, to keep log tidy. You can however select different Verbosity level.
To record log messages about media streams you can either lower the verbosity level, or raise the Mediastream log level to above verbosity level.
You can filter the SIP log to record only certain headers, methods or IP addresses:
- Log SIP header fields - Enter the name of the SIP header fields (e.g. From, To) you want to record into the SIP Log (Verbosity level has to be “info” or “debug” to use this feature). '*' can be used to record the complete SIP message with all headers.
- Log SIP methods - Filter logging of SIP messages by method. If the word “not” is prepended all SIP messages that not matches the methods listed will be logged. Examples: “not REGISTER” or “INVITE ACK BYE CANCEL”.
- Log only communication with IP addresses - Filter the logging of SIP messages. Only SIP messages sent or received to the given IP addresses are recorded into the SIP Log.
- Log internal SIP messages - SIP messages may be sent to/from internal applications of the box, when this checkbox is checked all messages will be logged. Otherwise only message sent out or received from the network will be shown.
This section contains also settings for the logging for telephone ports and built-in IVR units (auto attendant, conference unit, voicemail unit, testagent unit):
- Log telephone port and IVR unit calls - Use this checkbox to get a logging for each start and end of a call where a telephone port (FXS/FXO) or an IVR unit is an endpoint.
- Telephone ports and IVR units debug messages - Use this checkbox to get a lot of debug output for each call where a telephone port (FXS/FXO) or an IVR unit is an endpoint. Should only be enabled for debug purposes, because it needs quite a lot of processing power.
The SIP log can be viewed on the SIP log page or forwarded to various receivers, see below.
VPN Log
The VPN log records Virtual Private Network events. Visible only if VPN license is installed into the unit.
Usually debug messages are not recorded into the VPN log. You can however include them too if support requests you to.
The VPN log can be viewed on the VPN log page or forwarded to various receivers, see below.
Call Log
The call log records information about SIP calls made through the unit.
Call detail recording level - Select the amount of information recorded for each call:
- Off - No information is logged.
- Basic - Information about call participants, duration, termination reason, etc is recorded.
- Including media statistics - Calculate and store information about voice quality too.
Log local calls too - Log information about local calls (made between LAN phones) too. (Same as setting “Always record route” on SIP advanced page.)
The Call log can be viewed on the Call log page or forwarded to various receivers, see below.
Distribute
You can distribute (forward) entries recorded into the logs to other recipients such as syslog servers:
Save to File
You can save a snapshot of current contents of all logs into a file on your PC. It is not a continuous logging, just a momentary snapshot.
Log to USB memory
Log entries in all logs can be logged to files on an attached USB memory. Logging starts automatically when an inserted USB memory has a /log folder on it. Log files are created for each log (system/firewall/SIP etc) and filled with log entries as they occur. New log files are created for each power on.
![]() If logging does not start then check that the folder is named /log (not /Log !), the file system of the USB memory is FAT32, and Read only access is disabled on USB Web server page.
If logging does not start then check that the folder is named /log (not /Log !), the file system of the USB memory is FAT32, and Read only access is disabled on USB Web server page.
Forward to syslog server
Log entries in all logs can be forwarded to remote syslog servers.
Contents of the system and firewall logs can be sent to the primary syslog server.
Contents of the other logs can be sent to that primary syslog server too, or to other dedicated syslog servers.
![]() WARNING! Logging all packets in the firewall log, and enabling forwarding of firewall log to a syslog server generates one extra packet of data traffic for each and every packet received or sent by this unit! This not only reduces performance/bandwidth of this unit but your entire network! Use with extreme care!
WARNING! Logging all packets in the firewall log, and enabling forwarding of firewall log to a syslog server generates one extra packet of data traffic for each and every packet received or sent by this unit! This not only reduces performance/bandwidth of this unit but your entire network! Use with extreme care!
Do not forward ACCEPT log entries - To reduce network traffic you can set “Firewall Log” above to “Show all packets”, enable “Forward firewall log to primary syslog server” and enable this setting. Then all sent/received packets will be logged in the unit's internal firewall log, but only ERROR/DROP/DENY entries will be forwarded to the syslog server.
Send as e-mail
Log entries in all logs can be mailed to an e-mail account. To be able to send e-mails you must supply address of an SMTP server on the E-mail page.
For performance reasons log entries are not mailed one-by-one, but as log files containing several log entries. Thus reporting through e-mail can be delayed until more log entries are collected.
The generated e-mail contains the severity level of the most severe event logged in the attached log file. Please notice that the message always lists only ONE log entry - there might be more log lines in the attached log file with similiar severety!
You can limit the amount of logs e-mailed by selecting what severity level of an event must have been occurred for an e-mail to be generated. (As the firewall log has no severity levels it cannot do such filtering.)
Forward to SNMP server
Log entries in all logs can be forwarded, embedded in SNMP traps, to a remote SNMP server.
By specifying a community and IP address SNMP traps can be generated for log events with selected severity levels or higher.
Log traps sent have OID .1.3.6.1.4.1.1218.1.5.0.0
Installing Internet Gate's customer specific MIB makes receiving log traps easier. Read more here