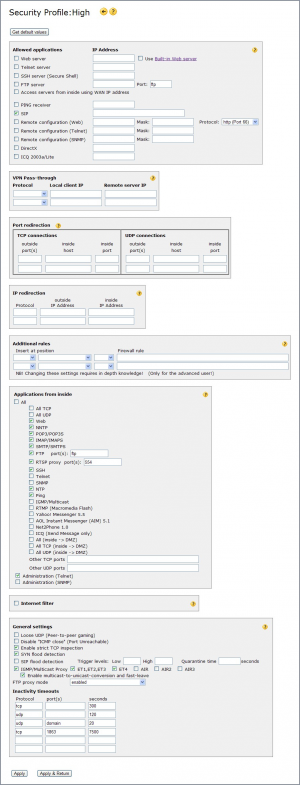
Security Profile
The Security profile page allows you to edit any of the security profiles High, Low or AltConf.
![]() Even though all three profiles are editable you are recommended to edit only profile AltConf (Alternative Configuration), and leave High and Low unaltered.
Even though all three profiles are editable you are recommended to edit only profile AltConf (Alternative Configuration), and leave High and Low unaltered.
![]() For some hints concerning port openings etc., see here.
For some hints concerning port openings etc., see here.
Press Get default values to restore the security profile to its original values (then click “Apply”).
The main groups of settings controlling the firewall are:
Allowed applications
controls opening of outside ports on the firewall. Thus specifying what data coming from the Internet to be allowed through the firewall, and to which PC to forward (NAT) the data to.
Web, Telnet, SSH, FTP server Check box if you have any of these servers on your LAN, and you want computers on the Internet to be able to access them. Enter the server's local IP address. Check “Use Built-in Web server” to use this unit as your web server to the Internet (see also here). The FTP server Port field controls your external FTP port - your FTP server shall still listen to port 21! Telnet SSH FTP
Access servers from inside using WAN IP address Check box if you want to be able to access your web, telnet, ssh or ftp server from inside using your global IP address. If box is not checked the servers can only be reached using their local IP address.
PING receiver Check box if you want ping-requests from the Internet answered by a PC on your LAN. Enter the PC's LAN IP address, or 127.0.0.1 to make the Internet Gate itself answer.
![]() Extreme security risk! Answering to ping-requests from Internet reveals your presence for attacks, e.g. “flood-pinging”. Ping
Extreme security risk! Answering to ping-requests from Internet reveals your presence for attacks, e.g. “flood-pinging”. Ping
SIP Check box if you want the SIP functionality to be allowed through /answered. The IP address field could be filled in to allow only some IP addresses to send SIP traffic to the unit. Several IP addresses could be entered by using comma sign, dash or subnet notation.
Example: “1.2.3.4 - 1.2.3.8, 5.5.5.5, 6.7.8.9/24”
Remote configuration Web/Telnet/SNMP Check box(es) if you want the configuration web interface (these pages), the command line interface (Telnet with port 57) or the SNMP server resp. to be accessible from the Internet. The IP address/mask fields could be filled in to allow only one or a few IP addresses to access the configuration. Choose if you want to use http (with port 66), https (with port 78), or both of them, when accessing the web pages from outside.
(![]() Security risk!) Telnet SNMP
Security risk!) Telnet SNMP
DirectX Check box if you want to play games using the Microsoft DirectX communication module: (Ages of Empire, Midtown Madness, Motocross Madness, most Microsoft-games, many Windows-games) DirectX
Multi-user gaming support: Some games where many users can play with each other over the Internet demand that the firewall allows non-conventional data traffic. The “Lo” security profile is pre-configured for most such games (as “All” is checked at “Applications from inside” and “loose UDP” is enabled). Some DirectX-based games though might demand that the DirectX checkbox is enabled.
ICQ 2003a/Lite Check box if you want to communicate with other ICQ users.
![]() Port range is set to 1024-2048, you must specify this range in ICQ. Follow the link under “Read more online” (bottom of page) for instructions.
Port range is set to 1024-2048, you must specify this range in ICQ. Follow the link under “Read more online” (bottom of page) for instructions.
![]() Security risk (opens up a large hole in firewall)! Not recommended. If you only want to utilize the “Send Message” feature check ICQ box under “Applications from inside” instead (more secure).
Security risk (opens up a large hole in firewall)! Not recommended. If you only want to utilize the “Send Message” feature check ICQ box under “Applications from inside” instead (more secure).
VPN Pass-through
controls VPN tunnels going through the firewall, thus VPN connections that are not terminated in the unit itself.
Port redirection
Manual opening of outside ports on the firewall. Port numbers TCP UDP
If you enter one outside port , you can enter a different inside port to redirect the data stream. If you leave inside port empty, the data will be sent to the same port number as opened.
If you enter a range of outside ports , leave inside port empty. The data will be sent to the same port numbers on the PC. A range of ports can be entered using the “-“ sign, e.g. “5011-5013”.
It is recommended to enter one port range instead of multiple entries. Thus open ports 5011-5013 instead of opening port 5011 and 5012 and 5013.
Once an incoming port that is open receives data, a flow is created, that allows data to be both sent and received using that port. There is no need to explicitly open that port for outgoing data as well. The port redirection rules are only needed for the initial first reception of the first packet received at that port from the Internet.
IP redirection
Manual IP protocol/address redirections from WAN to LAN. (only for advanced users) Redirections selected in priority order, 1:st row first.
Protocol Protocol number or (for common protocols) name. Leave blank for “all protocols”.
outside IP address Global IP address that is to be redirected. Only if you have received more than one global IP address from your Internet provider. Else leave empty.
inside IP address IP address of LAN PC that should receive the data traffic.
Additional rules
Manually written rules. You can hand write firewall rules in a special syntax allowing advanced users full control over firewall behaviour.
Read the firewall rules tutorial for learning how to write firewall rules manually.
Insert at position Firewall ruleset to add rule to, as seen on the Firewall Rules status page. (![]() All three fields MUST be chosen!)
All three fields MUST be chosen!)
- pre - add rule before the automatically generated ones - the rule will have higher priority.
- post - add rule after the automatically generated ones - the rule will have lower priority.
- subst - substitute automatically generated rules with the entered one. WARNING! No rules will be auto-generated for that ruleset!
Firewall rule ONE firewall rule to add at specified position.
To add multiple rules to a ruleset enter multiple entries. To delete entries set their position fields to empty.
Applications from inside
controls opening of inside ports on the firewall. Thus specifying what data coming from your PCs to allow go out to the Internet.
All - Allow all outgoing data traffic to pass through. No filtering. (![]() Security risk! Not recommended!). If not checked, the following applications/ports may be selectively allowed:
Security risk! Not recommended!). If not checked, the following applications/ports may be selectively allowed:
All TCP - Allow all outgoing TCP packets to pass through. (Not recommended)
All UDP - Allow all outgoing UDP packets to pass through. (Not recommended)
Web - Allow web access (“surfing”).
NNTP - Allow access to newsgroups. NNTP
POP3 - Allow reception of e-mail. POP3
IMAP - Allow reception of e-mail. IMAP
SMTP - Allow sending e-mail. SMTP
FTP - Allow file transfers on selected port(s). FTP
RTSP proxy - Allow listening to web radio/tv on selected port(s) by using the builtin RTSP proxy. RTSP
SSH - Allow logging in to servers using Secure Shell. SSH
Telnet - Allow logging in to servers using the Telnet protocol. Telnet
SNMP - Allow supervision and control of networks using SNMP. SNMP
NTP - Allow time synchronization. NTP
Ping - Allow outgoing ping (a LAN PC pinging to a PC on WAN / Internet). Ping
IGMP/Multicast - Allow reception of multicasted data streams.
Check also the IGMP/Multicast Proxy settings under General settings on this page. IGMP Multicast
RTMP (Macromedia Flash) - Allow audio/video streams by a Flash player. RTMP
Yahoo! Messenger 5.5 - Check box if you want to communicate with other Yahoo! Messenger users.
AOL Instant Messenger (AIM) 5.1 - Check box if you want to communicate with other AOL Instant Messenger users.
Net2Phone 1.0 - Check box if you want to utilize the Net2Phone application.
ICQ (Send Message only) - Check box if you only want to send messages to other ICQ users. To utilize the more advanced feautures check ICQ box under “Allowed applications” instead.
inside → DMZ - Allow all, all TCP or all UDP traffic from LAN to DMZ.
Other TCP ports - Open specific port numbers (only for advanced users) TCP
(several ports can be entered, separated by comma, along with port ranges “xxx-yyy”)
Other UDP ports - Open specific port numbers (only for advanced users) UDP
(several ports can be entered, separated by comma, along with port ranges “xxx-yyy”)
Administration (Telnet) - Allow access to command line interface. Telnet
Administration (SNMP) - Allow access to internal SNMP Server. SNMP
Internet filter
Also called “Parental control”. Block visits to certain Internet sites. Denies access to certain Internet sites - users behind this unit cannot access them. You can also deny download of certain file types.
Internet filter Check box to enable filtering of web accesses.
Block sites Enter a list of sites (comma separated) users should not be able to access. Compares the hostname part of the URL - the part before the first ”/”. Do not include the starting “www.” part. Sites with their full name matching are blocked. If you do not specify the top-level domain all domains are denied.
Example: “youtube.com,google” stops access to www.youtube.com, google.com, and google.co.uk, but allows youtube.co.uk, googlefight.com and en.wikipedia.org/wiki/google
Block IP numbers Block use of IP address in URL (eg http://213.136.58.99)
Block filetypes Enter a list of file extensions (comma separated) users should not be able to download. Compares the path part of the URL - the part after the first ”/”. Include the starting dot. File types exactly matching the extensions are blocked.
Example: ”.exe,.gz” stops downloads of executable and gz-compressed files, though .gzip files can still be downloaded.
Allow all browsing from IP addresses Enter a list of IP addresses (comma separated) users can surf unlimited from. Hosts with listed IP addresses can still access any site on the Internet regardless of Internet filter settings.
![]() By enabling Log blocked access attempts on the Log Configuration page all web access attempts blocked by the Internet filter will be logged into the system log.
By enabling Log blocked access attempts on the Log Configuration page all web access attempts blocked by the Internet filter will be logged into the system log.
General settings
Other security settings:
Loose UDP Loose UDP means information is coming back from different port on remote server than it has been sent to. Many games use “loose UDP” for communicating between several users over the Internet: e.g. BattleZone1.4, Dark Reign1.4, Diablo, HeavyGear2, Quake I/II, StarCraft, WorldCraft, and most of the games from Activision Check the box to allow such traffic to pass through.
Disable “ICMP close” (Port Unreachable) Avoid “UDP connections” from being closed by ICMP Port Unreachable messages. ICMP
Enable strict TCP inspection Uncheck this if encountering compatibility problems with certain servers. By disabling TCP inspection the firewall becomes a bit more “forgiving” with some common TCP rule violations some servers do when overloaded. TCP
SYN flood detection Checking this box will protect against an attack using flooding with SYN messages (SYN is the initial message for opening a TCP connection). TCP
SIP flood detection Detect SIP DoS attacks and block sender IP address. A sender of SIP messages will be blocked if the rate of SIP packets exceeds the High trigger level (packets/s) and unblocked when the rate goes down to Low. If Quarantine time is set the sender will be blocked for an additional number of seconds. DoS
IGMP/Multicast Proxy
If enabled multicasted data streams are proxied, delivered only to the subnet the requesting client is on. If this proxy is disabled all received multicast data streams are forwarded to all local subnets.
ET1,ET2,ET3, ET4, AIR Select what local interfaces are allowed to receive multicasted data streams. This setting affects only interfaces categorised as “inside” on the Network Configuration page - DMZ and other interfaces never receive multicast regardless of these settings.
![]() You must enable IGMP/Multicast at Applications from inside on this page to allow multicast traffic through the firewall!
You must enable IGMP/Multicast at Applications from inside on this page to allow multicast traffic through the firewall!
![]() The Internet connection of the multicast proxy is by default the current WAN interface, unless specified otherwise on the Extra WAN Interfaces page.
The Internet connection of the multicast proxy is by default the current WAN interface, unless specified otherwise on the Extra WAN Interfaces page.
IGMP Multicast
FTP proxy mode Select if FTP traffic should be subject to the internal FTP proxy. “Disabled” means that only address translation (NAT) is performed.
![]() FTP traffic is still admitted/rejected based on the other FTP settings on this page. FTP Proxy
FTP traffic is still admitted/rejected based on the other FTP settings on this page. FTP Proxy
Inactivity timeouts Close the connection if no data has been transmitted for the specified time. Specific timeouts for particular ports/protocols may be added.