Certificates
By using certificates instead of pre-shared keys a much higher level of security can be achieved. Certificates are used to verify the other end of an IPSec connection is a known peer, not an imposter.
Read more: certificates
The Internet Gate can use certificates created by other authorities, create its own certificates, or even create certificates for clients connecting to it.
| |
|---|
| To avoid loosing your certificates make sure you make a backup copy using the Backup to file button on the Administration page. |
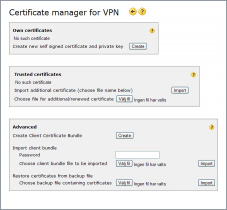
You can access the VPN Certificates page by clicking the Certificates link at the bottom of the IPSec Overview page.
Own and trusted certificates
There are two groups of certificates:
Own certificates are your own certificates that you can give to other IPSec peers, or use to sign certificates with. You use them to identify yourself to the remote peer by presenting to it the certificate you once have given a copy of to it.
Trusted certificates are certificates that you have received from other IPSec peers. You use them to verify a connecting peer's identity – if it is a valid peer then it will use the same certificate you once have received from it.
Certificate authorities
You can either buy your certificates from external certificate authorities or make your own.
Both methods are equally secure, but using external certificate authorities makes certificates more traceable. Usually larger corporations demand use of certificate authorities, while a small company might just as well use self-signed certificates.
Certificate exchange
To set up an IPSec connection that uses certificates the two IPSec peers need to exchange certificates with each other. The certificate exchange is off-media – the certificates stored in files and exchanged between the peers using disc, USB memory stick or e-mail (not recommended) long time prior they connect for the first time (days or weeks before).
Client Certificate Bundle
To simplify managing an IPSec infrastructure where the Internet Gate is an IPSec server you can create Client Certificate Bundles. Then clients don't need to send their certificates to the Internet Gate server – it generates a suitable certificate for them and packs it together with its own public certificate into one single file to be loaded into the clients.
Own certificates
These are your own certificates that you can give to other IPSec peers, or use to sign certificates with. You use them to identify yourself to the remote peer by presenting to it the certificate you once have given a copy of to it.
You can either create your own certificate, or import one created by some other certificate authority.
Most users only need one own certificate that is given to all remote IPSec peers. You are however free to create/import multiple certificates if needed.
Create your own certificate
You can create your own self-signed certificate using the Create button on the Certificate manager page.
In the window that appears you enter details about the certificate:
Subject name (mandatory) unique, descriptive name of the person or purpose the certificate is for.
Organisation (optional) organization the certificate is for. (For example your company.)
Organisation unit (optional) organization unit the certificate is for. (For example your department.)
DNS name (optional) DNS domain the certificate is for. (For example your dynDNS domain.)
E-mail (optional) e-mail address of contact person for the certificate.
IP Address (optional) IP address the certificate is for.
The signature algorithm used should be RSA/SHA1 for almost all users, except if the remote peer has specifically specified DSS signatures as IKE authentication mode.
The created self signed certificate and private key are stored in your Internet Gate. You are strongly recommended to immediately create a backup copy of them using the Backup to file button on the Administration page.
![]() Certificates are erased by reset to factory defaults!
Certificates are erased by reset to factory defaults!
You give away your own certificate to whoever remote IPSec peer you want to connect or want to be able to be connected by. The Export button next to your certificate on the Certificate manager page creates a file containing your certificate that you can give away. (It does not contain your private key, as you should never give away your private key.)
The created file is of suitable format for importing into most common IPSec programs.
Using your own certificate
You use your certificate to identify yourself with when connecting to a remote IPSec gateway.
The IPSec Settings page reached from the simplified IPSec Overview page (by “Add” or “Edit/view” buttons) always use your first own certificate when creating new connections that use certificates as authentication. You do not need to specify own certificate, only the trusted one.
On the VPN peer settings page reached from the advanced IPSec overview page you can specify what own certificate to use using the Certificate dropdown under the “Identity – Local (this) gateway” headline.
Then you also need to specify which of the certificate's fields you want to use for identification:
Id type: ASN.1 Dist. Name, ID: Use ASN.1 in cert is the most common choice. This uses the Subject name field in the certificate as identification.
Id type: Domain name and E-mail (user DN) both demands ID: Other, specify: to be selected, and the same entry as in the certificate to be entered manually.
You also must change Authentication Method in all three preferences (under the “Key exchange” headline) to RSA signatures. (If the certificate was issued using signature algorithm DSA/SHA1 then you need to specify DSS signature here.)
Local (own) and remote (trusted) certificates must both use the same Authentication method. You can't mix certificates and pre-shared key for authentication.